Introduction
In an increasingly interconnected world where digital communication is ubiquitous, the need for robust encryption methods has become paramount. Traditional cryptographic techniques, while effective, face growing challenges from the advent of quantum computing, which threatens to render many current encryption standards obsolete. However, amidst these concerns, a beacon of hope shines brightly in the realm of quantum cryptography – a revolutionary field harnessing the laws of quantum mechanics to create unbreakable cryptographic systems.
Understanding Quantum Cryptography
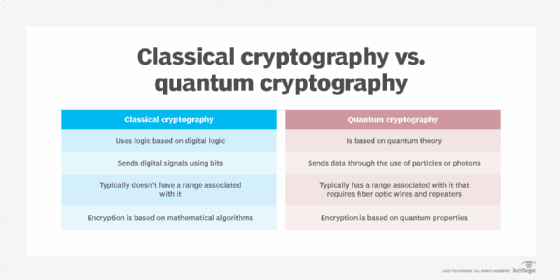
Quantum cryptography leverages the principles of quantum mechanics to achieve unparalleled levels of security in communication. Unlike classical cryptography, which relies on mathematical complexity for security, quantum cryptography exploits the fundamental properties of quantum physics, such as superposition and entanglement, to ensure the confidentiality and integrity of data transmission.
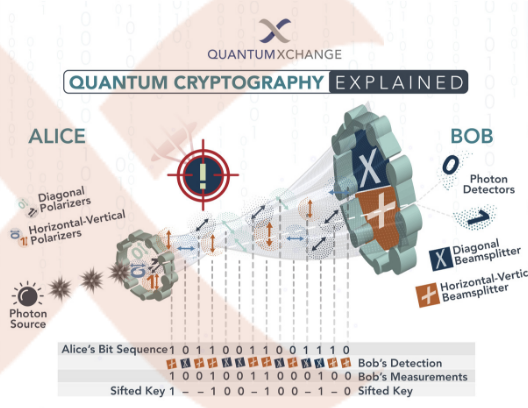
At the heart of quantum cryptography lies the phenomenon of quantum key distribution (QKD). QKD enables two parties, traditionally referred to as Alice and Bob, to establish a shared secret key with absolute security. This key can then be used to encrypt and decrypt messages, guaranteeing that any eavesdropping attempts will be immediately detected.
The Principle of Quantum Key Distribution
The cornerstone of QKD is Heisenberg’s uncertainty principle, which states that the act of measuring a quantum system invariably disturbs it. In the context of QKD, this principle is leveraged to detect the presence of an eavesdropper, often referred to as Eve.
When Alice sends quantum bits, or qubits, to Bob, Eve may attempt to intercept them. However, due to the uncertainty principle, any attempt by Eve to measure the qubits will inevitably alter their quantum states, alerting Alice and Bob to her presence. This detection mechanism ensures that the shared key remains secure, as any tampering with the qubits is immediately detected.
Types of Quantum Cryptographic Protocols
Several protocols have been developed to implement QKD effectively. One of the earliest and most well-known protocols is the BB84 protocol, proposed by Charles Bennett and Gilles Brassard in 1984. BB84 relies on the transmission of polarized photons to establish a shared key between Alice and Bob. Other notable protocols include E91, developed by Artur Ekert in 1991, and the more recent measurement-device-independent quantum key distribution (MDI-QKD) protocol, which offers enhanced security guarantees.
Challenges and Advancements in Quantum Cryptography
While quantum cryptography holds great promise for the future of secure communication, several challenges remain. One significant obstacle is the practical implementation of QKD over long distances, as quantum systems are inherently susceptible to noise and loss. Researchers are actively exploring methods to overcome these limitations, such as the development of quantum repeaters and satellite-based QKD networks.
Furthermore, the emergence of quantum computers poses a potential threat to current cryptographic systems, including those based on quantum cryptography. To address this concern, researchers are investigating post-quantum cryptography schemes that remain secure even in the presence of quantum adversaries.
Despite these challenges, recent advancements in quantum cryptography offer renewed optimism. Breakthroughs in quantum technology, coupled with innovative cryptographic protocols, are paving the way for a future where secure communication is not only achievable but inherent in the fabric of our digital infrastructure.
Conclusion
In an age where data breaches and cyberattacks are all too common, the importance of robust encryption methods cannot be overstated. Quantum cryptography represents a paradigm shift in cryptographic techniques, offering unparalleled security guarantees rooted in the laws of quantum mechanics.
As we continue to navigate an increasingly digitized world, the development and adoption of quantum cryptographic solutions will be crucial in safeguarding sensitive information and ensuring the privacy of individuals and organizations alike. While challenges remain, the promise of quantum cryptography shines bright, illuminating a path towards a future where secure communication is not just a possibility but a reality.